- What is VPN?
- VPN Protocols
- VPN Service Providers
- Is VPN Safe and Anonymous?
- VPN Kill Switch and Connection Drop
- DNS Leak Considerations
- VPN Encryption Test
- VPN Router Settings
- Free VPN Services
- Recommendations
1. What is VPN?
VPN stands for Virtual Private Networks and essentially was created for secure communications between two ends. A good example would be working from home when you connect to your place of work network. Another example, if you are subscribing to a VPN service provider then you will be connecting to the internet anonymously by a VPN tunnel. The principle behind VPN technology is simple – all communications are encrypted making the contents secure against interception by a third party.
More and more people are using VPN services due to increased monitoring of internet activities. There are legal requirements in most countries that Internet Service Providers (ISP) should log activities of internet users. There is a good reason for these requirements since it enables authorities around the world to combat crimes and law breakers. However, many people regard this monitoring as an invasion of their privacy and hence resorts to using a VPN service. On other occasions, users may want to stream legal contents across different regional locations which is normally not possible without the use of a VPN service.
In this article we will explore the important aspects of DNS leak and Kill Switch technologies as they can impact the effectiveness of any VPN service and compromise your security. We have used the Merlin AsusWRT custom firmware as a reference in this discussion. However, similar setup procedure will apply to oter custom firmware that you may wish to consider.
2. VPN Protocols
The main VPN Connection Protocols are listed below:
- PPTP: Point-to-Point Tunnelling Protocol is one of the oldest VPN communication protocols. Its security algorithm has been compromised making it less secure for more demanding environments. However, its advantage of faster speeds may suit some users although its support by VPN providers is being gradually phased out.
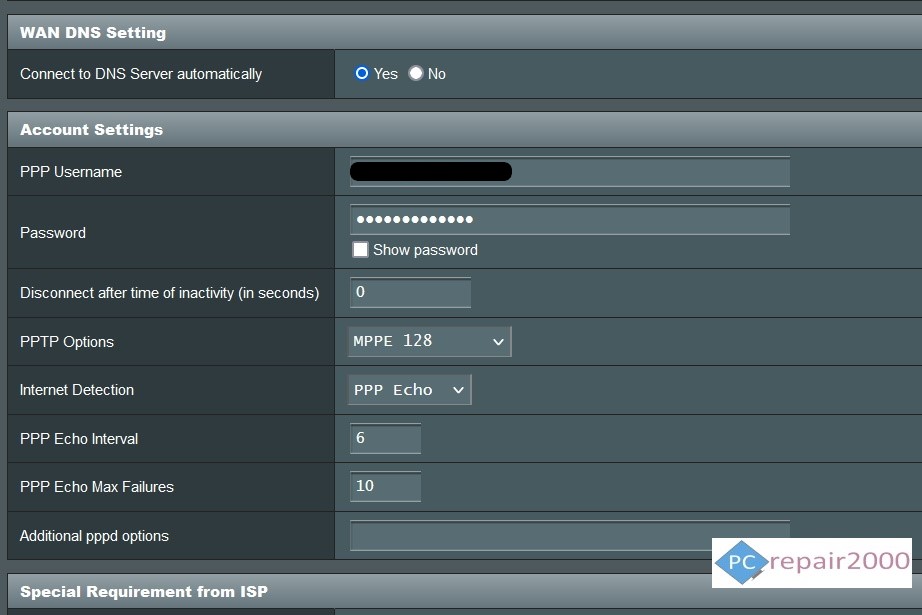
PPTP Connection Settings
- L2TP/IPSec: Layer 2 Tunnelling Protocol and Internet Protocol Security is another VPN communication protocol. L2TP provides the communication tunnel while IPSec provides the encryption. It must be noted therefore that using L2TP protocol by itself does not provide any security in the communication. L2TP is still in use since it is still secure and provides a good connection speed.
- Open VPN: It is an open source VPN protocol and currently the most popular due to very strong encryption of WES-256 bit key. This protocol is the most recommended for users as it provides the highest level of security. However, the trade-off is a slower connection speed.
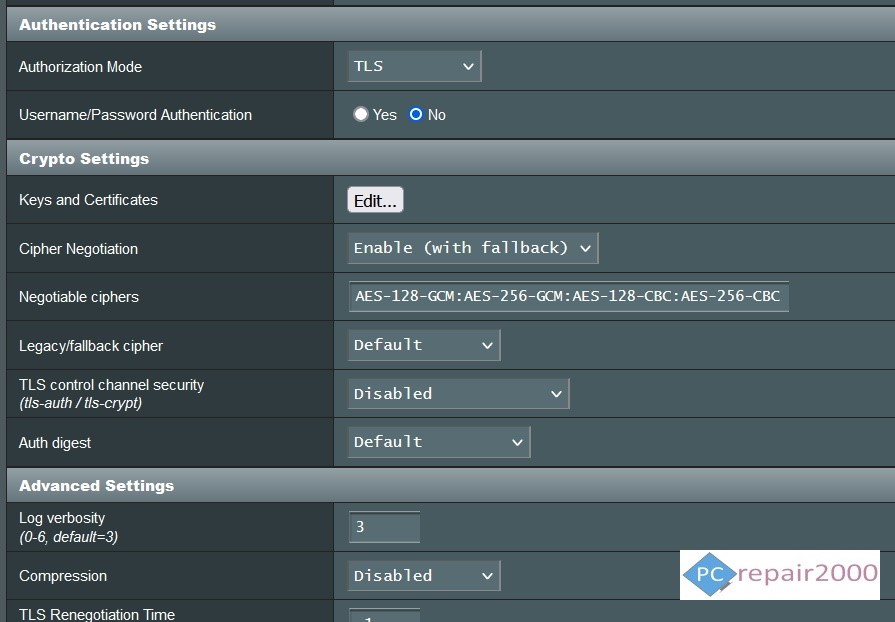
OpenVPN Connection Settings
- IKEv2: Internet Key Exchange Version 2 is another VPN protocol similar to L2TP as it must be paired with IPSec for communication encryption. It suitable for wireless communication and mobile users and can be open source.
- SSTP: Secure Socket Tunnelling Protocol is a propriety VPN protocol created by Microsoft and mainly used in the Windows operating systems family. It has a high level of security at AES-256 bit key but lacks compatibility with third parties.
3. VPN Service Providers
Due to increased demands on VPN services, there are currently an extensive range of services available to choose from. Of course, not all VPN service are created equal hence you should do your homework and research your chosen VPN service provider in advance. This effectively means trying to establish the following:
- Does the VPN service provide sufficient connection speeds? Many of the cheaper VPN providers struggles to provide faster connection speeds due to increased number of subscribers and possible lower level of investments in hardware and infrastructure. Please bear in mind that your VPN connection speed is always going to be lower than your maximum connection speed to your ISP. This is usually due the overhead of encrypting communication messages. However, this reduction in speed should only be a small fraction and therefore you should still have a usable internet speed.
- What is the level of the provided privacy and anonymity? After all, the reason for using a VPN service is maintain your privacy and prevents monitoring of your internet activities. Many VPN service providers publish an audit report that details the level activities level for their users. It is worth exploring online reviews and customers feedback regarding your chosen VPN provider.
- List of Main VPN Providers:
Express VPN: Expensive, Fast Connection Speeds, Kill Switch, Good support via chat.
Nord VPN: Good Speed, Kill Switch, Large number of servers, No logs.
Private Internet Access: Ad-Blocker feature, Good speed servers.
Cyber Ghost: Up to 7 devices simultaneously, 45 days money back guarantee.
SurfShark: Good service, 30 days trial.
IPVanish: Good speed, large number of servers, No traffic logs.
4. Is VPN Safe and Anonymous?
To answer this question, you need to explore two important factors:
- Your chosen VPN service provider activities logging procedures. Many of the VPN providers have a zero-logging policy and this is what you should be looking for in terms of anonymity.
- The settings required for establishing the VPN connection. The second point is usually the most important to ensure that communications are not intercepted by your ISP. There are two different methods to establish a VPN connection:Client software VPN:
This application can run on Microsoft Windows 10, Microsoft Windows 11, MacOS, Chrome OS, Android, iOS, etc.. In this case you install the software or APP on a single device where you can make a VPN connection. You should also have access to a range of settings to enable fine tuning you connection, such as choosing the server location. The disadvantage of this type of connection is that this process must be repeated for every device that you own. Furthermore, your options for the settings are fairly limited.
VPN Client SoftwareRouter Setup VPN:
Using a router-based VPN connection. In this case you can connect all of your devices to the router and have a seamless VPN connectivity. There are no settings required for the client devices as all of the settings are performed on the router device. Unfortunately only a handful of routers are designed to make a direct connection to a VPN service. Amongst the most popular type of router are the WRT custom firmware based routers, AsusWRT Merlin firmware based, other routers that are compatible with special firmware that have been released by VPN service providers. - Local Laws and Legislations. Not all countries consider VPN service as a legal activity therefore it is important to check the local laws before using the service.
- Payment Methods and storage of details regarding account holders. Some VPN service providers offer anonymous payment methods such as crypto currencies or payment by vouchers. In this case no customer details will be stored in the service provider system. However, the majority of service providers will use the standard methods of payments via bank cards or PayPal.
5. VPN Kill Switch and Connection Drop
One of the most recent advances in VPN security is the introduction of Kill Switch technology. In short, this service refers to the ability of disconnecting the VPN connection when the encrypted communication channel breaks open. This is because when the encryption breaks, the contents of the communications and internet activities becomes visible to your ISP. Kill Switch technology aims to prevent exposing your communication contents should there be a temporary breakdown in the secure communication channel.
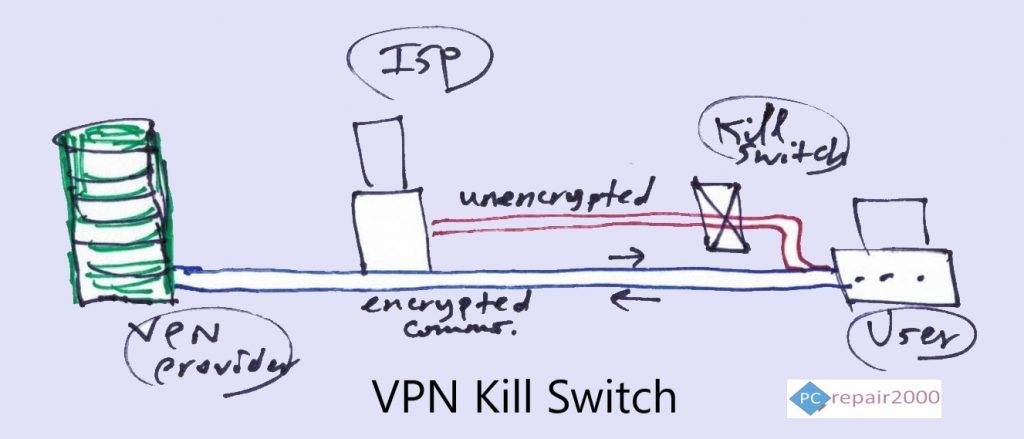
This security feature is usually incorporated into the client software or can be setup in the VPN routers. In some cases, a breakdown in the secure VPN connection will require a router restart to resume the VPN service.
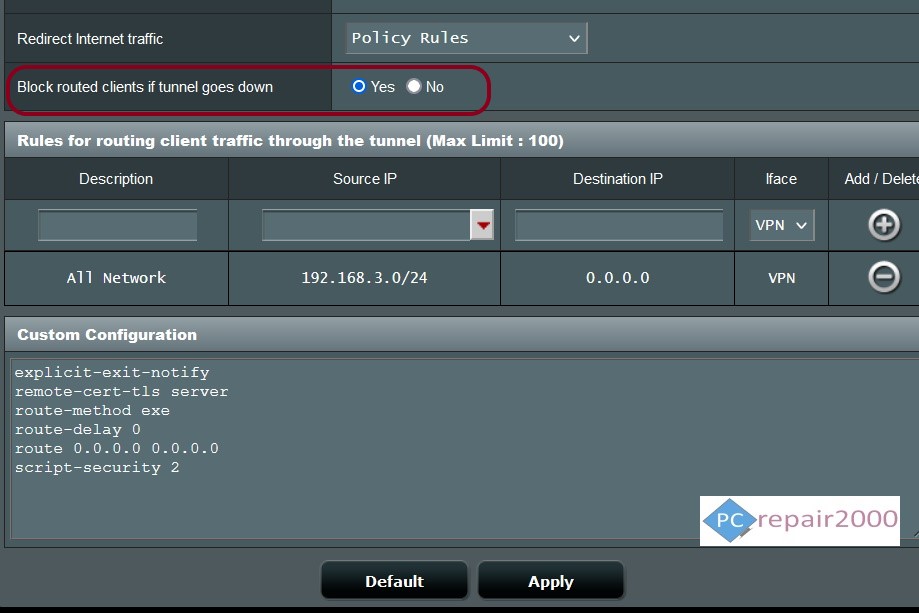
Kill Switch Settings – Merlin AsusWRT Custom Firmware
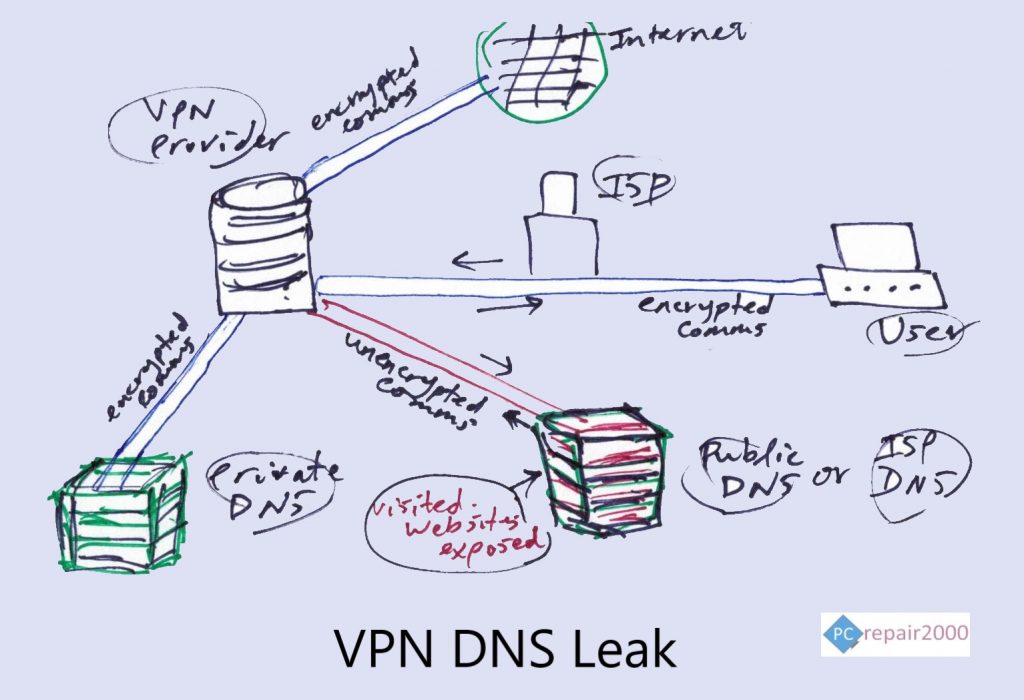
6. DNS Leak Considerations
DNS leak is one of the most underestimated feature when it comes to establishing a secure VPN channel. In general, most VPN providers will advice you to use well known public DNS servers or your ISP DNS servers for establishing a VPN connection. Two of the most widely used public DNS servers are:
- Google DNS Servers: 8.8.8.8 and 8.8.4.4.
- Open DNS Servers: 208.67.220.220 and 208.67.222.222

The reasons for using these servers is that it will allow the VPN provider to reduce its load and bypass some of the complexity in the infrastructure. However, in reality using a public DNS server exposes a weakness in the security of the communication channel. This is because in order to for the DNS server to provide you a resolution for website address request it must know the exact domain name in order to return the required IP address in unencrypted format. This process is known as DNS Leak and must be avoided if you want to establish a completely anonymous communication.
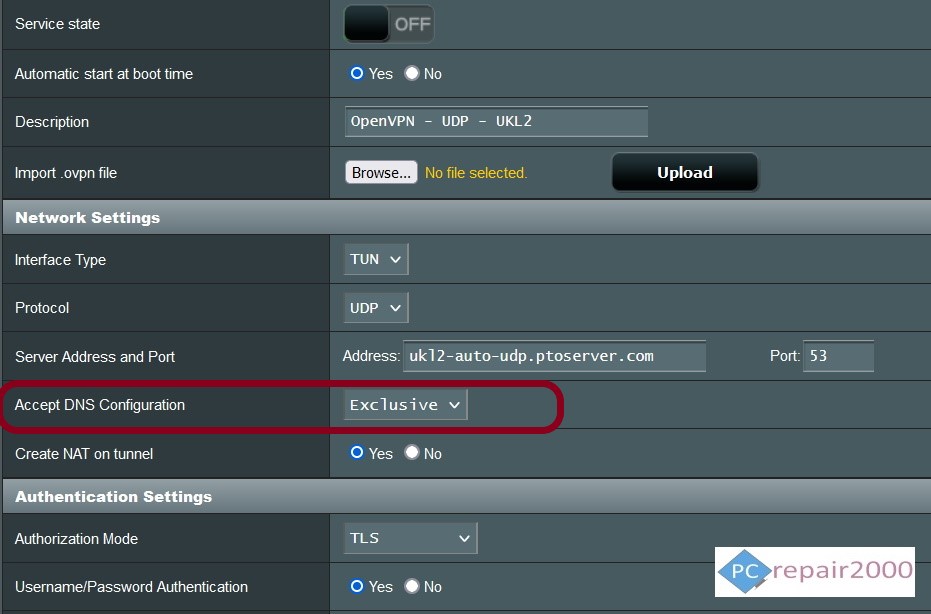
Avoid DNS Leak – Exclusive DNS Settings – Merlin AsusWRT
DNS leak test can be performed using some of the available utilites or websites online such as dnsleaktest.com, as shown in the picture below. The displayed reasults should show private DNS servers that belong to the VPN provider only, and no public DNS servers should be listed.
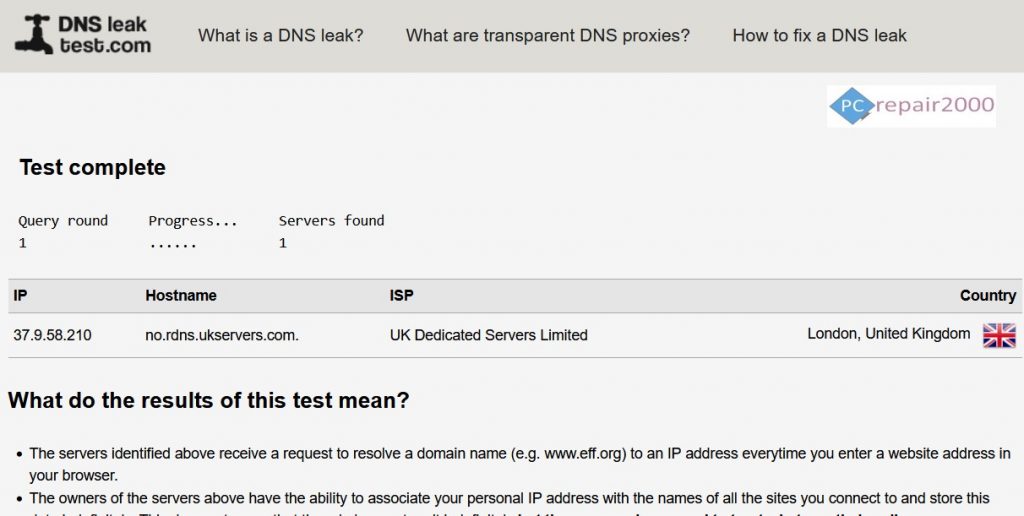
DNS Leak Test
7. VPN Encryption Test
You might think that all VPN communications should be encrypted. However, although this is mostly true should never take this for granted. The reason is simply because some VPN service providers want to reduce their communication overhead by disabling encryption making the VPN connection faster. This may sound counter productive but in reality it is a practice still in use by the lower end VPN service providers or most likely the Free VPN service providers. In a recent research it was found nearly 20% of the VPN providers was running unencrypted connections.
It is therefore your responsibility to ensure that your VPN communication tunnel is encrypted making it impossible to identify the contents of communication. There are two different approaches that you can take to test data encryption:
- Using software such as Glasswire or Wireshark. You need to download one of these software and follow the recommended procedure for tracing communication encryption.
- Using the simpler approach by trying to bypass a parental control or Google Search Filter. Simply setup an online parental control using your ISP provide filter or setup your browser in the Google restrict mode. If your communication is encrypted you should be able to bypass these filters otherwise your connection is not encrypted.
8. VPN Router Settings
There are mainly there different types of Routers that can handle VPN connections:
- WRT Routers: Uses custom firmware that are released for certain brands/Models. You need to check compatibility by visiting their website. It contains extensive settings for VPN connections including OpenVPN and other types of VPN protocols.
- AsusWRT Routers: This is a custom firmware released by Merlin which only support some of the Asus branded routers. Merlin Firmware is based on the standard Asus firmware with added customisations. There are good selection of options for setting VPN connections. It is easier to navigate and use when compared to the standard WRT custom firmware interface.
- VPN Providers Custom Firmware: All major VPN providers release custom firmware that is specific to their service and only supports some of the top end routers in the market. This option provides the most compatibility since the firmware is the most compatible by design.
AsusWRT Merlin Custom Firmware
9. Free VPN Services
There are now several hundreds of free VPN servers available on the internet. This is not surprising due to the increased popularity of the VPN service. However, since it is a free service there are important tradeoffs and negatives that you should be ware off:
- You connection will be slower that your internet speed. This is due to limited resources available, oversubscribing users or to force you to subscribe to a pais service instead.
- Your information will be used and shared with third parties.
- Your internet activities will be monitored for targeted advertising.
- In most cases, you have to register to use the free VPN Service.
As you can see there are no incentives for using the free VPN services, instead invest in a paid service for a more secure and reliable service. However, if you are still interested in trying some of these free VPN services, try these providers first:
Proton VPN: Free VPN service.
Hide Me: Free VPN Service.
Speedify: Free VPN Service.
10. Recommendations
VPN can be used positively to protect personal communication and maintain your privacy. In order to use this service and maintain your privacy you need to observe the following:
- Use a reliable paid VPN service, as this will maintain your security and privacy.
- Avoid Free VPN services, as in most cases your privacy is compromised.
- Ensure that your are using your VPN service provider’s DNS servers. Using public DNS servers, like Opens DNS or Google DNS will reveal the visited domains to the DNS servers owner.
- Look for a Kill Switch feature and activate it to protect your communication during a disconnection. When a VPN tunnel is interrupted normally your internet connection DNS reset to your ISP by default revealing your communication contents.
- Use a Custom Router, such as WRT or AsusWRT by Merlin to setup your VPN connection. This will allow you to share a single gate of protection for all of your devices.
